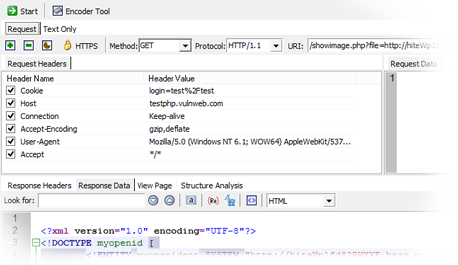
Take Automated Scanning Further
Most penetration testing professionals prefer to work with a whole scope of automatic and manual tools, not just a vulnerability scanner. Acunetix lets veteran testers as well as up-and-coming security researchers perform manual tests and then use the results of these tests to seed Acunetix scans. You can import data from the following security testing proxies:-
- Telerik Fiddler
- PortSwigger BurpSuite
- Postman

Automatic Web Application Firewall Configuration
Acunetix integrates with popular Web Application Firewalls (WAFs) to automatically create appropriate WAF rules. These rules protect web applications against attacks that target vulnerabilities found by the scanner. This allows you to temporarily prevent exploitation of high-severity vulnerabilities until you are able to fix them. Acunetix integrates with:- Imperva SecureSphere
- F5 BIG-IP Application Security Manager
- FortiWeb WAF
- Citrix Web Application Firewall
Integration and Extensibility
Acunetix features a powerful RESTful Application Programming Interface (REST API). The REST API allows you to access and manage scan targets, scans, vulnerabilities, reports, and other resources within Acunetix in a simple, programmatic manner using conventional HTTP requests.- Intuitive and powerful API endpoints
- Easily retrieve results and execute actions
- Seamlessly integrate Acunetix into complex, custom workflows and processes
Frequently asked questions
Penetration testers (pen testers) use a lot of automatic and manual tools. They use a vulnerability scanner to perform initial analysis and find typical vulnerabilities. Then, they perform manual penetration testing using tools such as Metasploit, W3AF, and many more. Tools are selected according to specific needs at the time.
Both penetration testing and vulnerability scanning are important. Vulnerability scanning should be performed first to save time that would be needed for manual penetration testing. Then, you should perform manual penetration tests for vulnerabilities such as business logic issues (that cannot be found using any automated tools).
Read about the relationship between penetration testing and vulnerability scanning.
The Acunetix web vulnerability scanner is a pen testing tool in itself: an automated penetration testing tool. However, Acunetix can also work with manual penetration testing tools by importing data directly from them.
The best way to use the Acunetix web vulnerability scanner as part of penetration testing is to start with an Acunetix scan. The Acunetix scan will give you a structure of the web application and find typical vulnerabilities. You can then use the structure of the web site to dig deeper manually if needed.
Read more about how to use Acunetix for penetration testing.
Recommended reading
Learn more about prominent vulnerabilities, keep up with recent product updates, and catch the latest news from Acunetix.

“We use Acunetix as part of our Security in the SDLC and to test code in DEV and SIT before being promoted to Production.”
Kurt Zanzi, Xerox CA-MMIS Information Securtiy Office, Xerox